

Cancel Anytime


















600+ Courses
Certificate of Achievement
4.9 Average Course Rating
Practical demo videos


Focused on mastering specific technologies or competencies, providing the in-depth knowledge and practical skills needed to excel.
Tailored to prepare you for specific job roles, offering a clear roadmap to build the necessary skills and knowledge for your career.

Focused on mastering specific technologies or competencies, providing the in-depth knowledge and practical skills needed to excel.

Tailored to prepare you for specific job roles, offering a clear roadmap to build the necessary skills and knowledge for your career.
Certificate of Achievement
80+ Learning Paths
4.9 Average Course Rating

Available with Pro+






Available with Pro+

Only Available with Pro+


The course helped me achieve my goals by expanding my knowledge in the field of cybersecurity and provided me with the necessary tools and techniques to be able to successfully perform as a cybersecurity engineer.
I am now better equipped for the job roles with clarity of expectations, responses, and defense mechanism to increase the security posture of my organization’s digital assets.
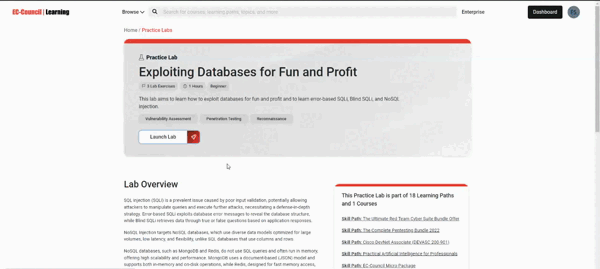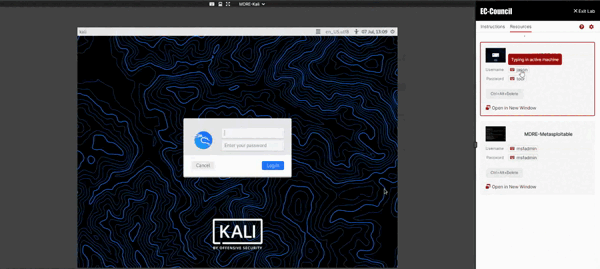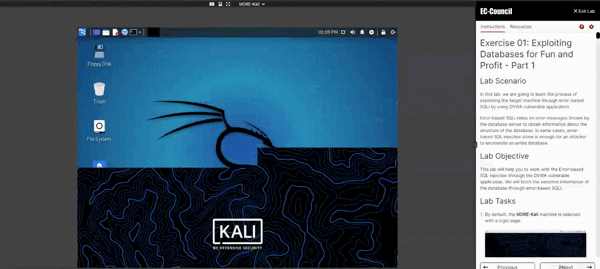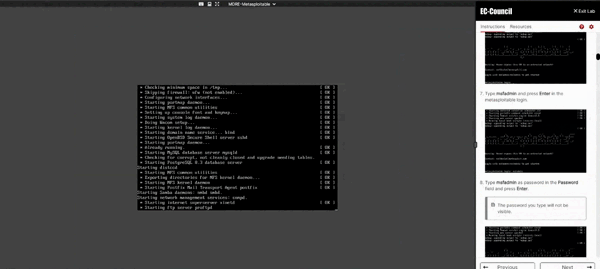
I have gained practical knowledge and how to use JSQL and run the commands on Kali Linux. This was very helpful course.
I loved this course! It not only helped me to review concepts and incidents I was learning about in a hands-on environment at work but now I am able to actually understand 1)What is happening, 2) Why it is happening and 3)How to avoid, minimize impact or correct the issues.
Thank you so much EC-Council Learning for such a wonderful opportunity, to learn essentials of ethical hacking. I am currently joined cybersecurity domain and this training gives me whole basic ideas about all the attacks type, vectors. I got in-depth knowledge on many attack types and their framework.
This is going to help me a lot at my new job, which requires much more live incident handling and malware analysis than what I'm used to.
This course was very in-depth on the practical application portion for pentesting/ethical hacking. This polished up my skills and was easy to understand.
I learned more about the available tools and methods involved with OSINT which will help in my cybersecurity career.
I am now able to use web proxies (Burp Suite and OWASP Zap) to find, exploit and report vulnerabilities as a pentester.
This course has a good illustration and explanation of incidence handling procedures and potential sources of evidence.
The course helped me achieve my goals by expanding my knowledge in the field of cybersecurity and provided me with the necessary tools and techniques to be able to successfully perform as a cybersecurity engineer.
I am now better equipped for the job roles with clarity of expectations, responses, and defense mechanism to increase the security posture of my organization’s digital assets.
I have gained practical knowledge and how to use JSQL and run the commands on Kali Linux. This was very helpful course.
I loved this course! It not only helped me to review concepts and incidents I was learning about in a hands-on environment at work but now I am able to actually understand 1)What is happening, 2) Why it is happening and 3)How to avoid, minimize impact or correct the issues.
Thank you so much EC-Council Learning for such a wonderful opportunity, to learn essentials of ethical hacking. I am currently joined cybersecurity domain and this training gives me whole basic ideas about all the attacks type, vectors. I got in-depth knowledge on many attack types and their framework.
This is going to help me a lot at my new job, which requires much more live incident handling and malware analysis than what I'm used to.
This course was very in-depth on the practical application portion for pentesting/ethical hacking. This polished up my skills and was easy to understand.
I learned more about the available tools and methods involved with OSINT which will help in my cybersecurity career.
I am now able to use web proxies (Burp Suite and OWASP Zap) to find, exploit and report vulnerabilities as a pentester.
This course has a good illustration and explanation of incidence handling procedures and potential sources of evidence.


"*" indicates required fields